Computational Policies
Lalana Kagal
MIT 6.805/STS085: Ethics and Law on the Electronic Frontier

|
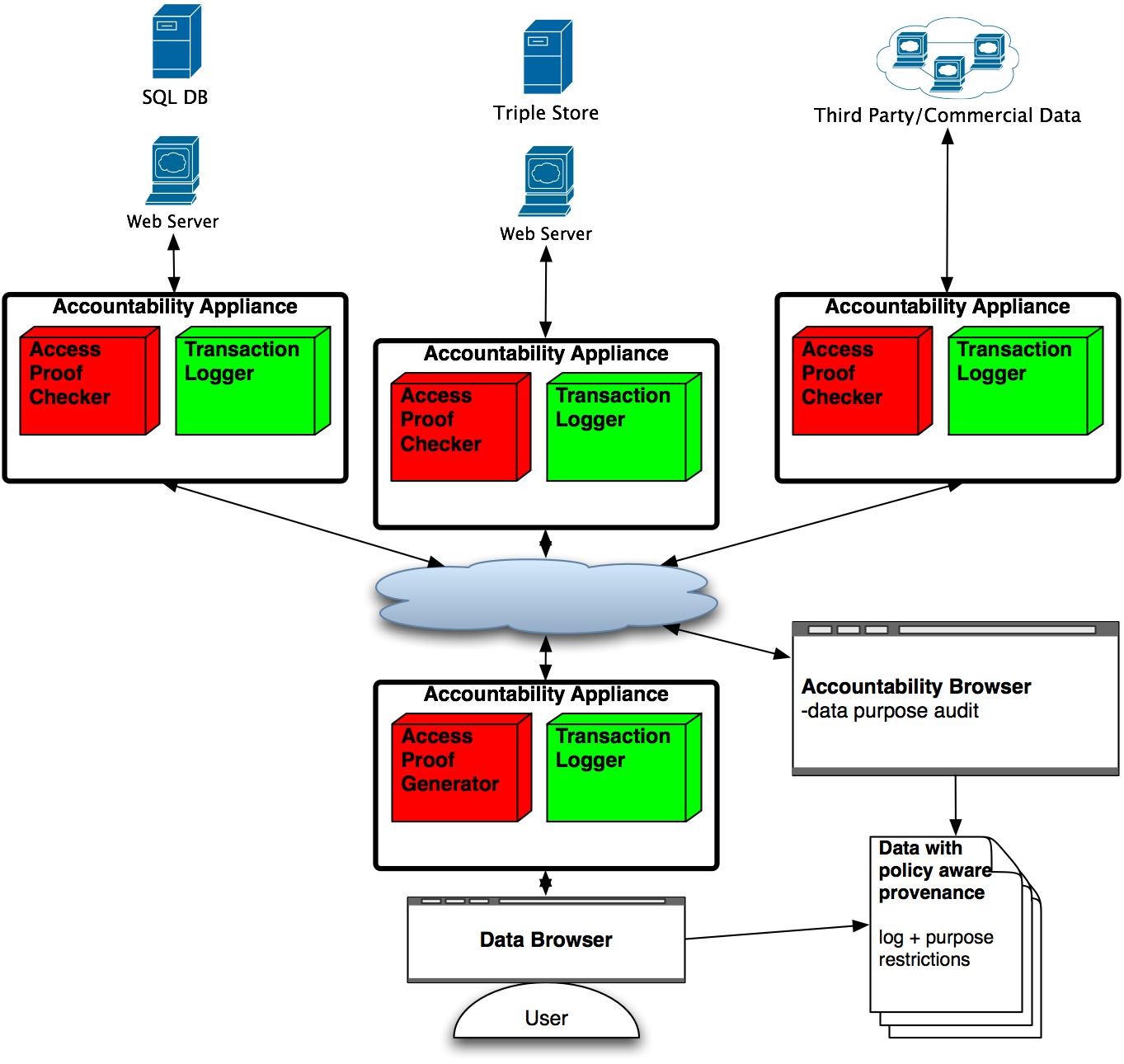
|
MIT Prox Card Data Policy: Prox card data can only the basis for an adverse consequence in a criminal investigation
:MITProxCardPolicy a air:Policy;
rdfs:label "MIT prox-card policy #1";
air:pattern
{
:U a air:UseEvent;
:refers-to :D;
air:purpose :P.
:D a :ProxCardEvent.
};
air:subrule
[
rdfs:label "MIT prox-card policy #2";
air:pattern { :P air:is-member-of pur:criminal-investigation };
air:assert { :U air:compliantWith :MITProxCardPolicy };
];
air:subrule
[
rdfs:label "MIT prox-card policy #3";
air:pattern { :P air:is-not-member-of pur:criminal-investigation };
air:assert { :U air:incompliantWith :MITProxCardPolicy };
]
.
