Rei+ : Specifying Privacy Policies
Lalana Kagal
July 2007
Decentralized Information Group
MIT Computer Science and Artificial Intelligence Laboratory
What is Rei+ ?
What do we mean by policy ?
What are privacy policies ?
Some Examples
Two approaches
Enforcement in open systems
Rei+ overview
Policy attributes
E.g. Everything that is not explicitly permitted is prohibited
APrivacyPolicy policy:defaultBehavior metapolicy:ExplicitPermImplicitProh.
E.g. In case of conflict, rules of negative modality (Prohibitions and
Dispensations) have priority over rules of positive modality (Permissions and Obligations)
VPrivacyPolicy policy:defaultModality metapolicy:NegativeModalityPrecedence
Deontic Rule: is used to create permissions, prohibitions, obligations and dispensations that govern the behavior of entities in the policy domain
|
|
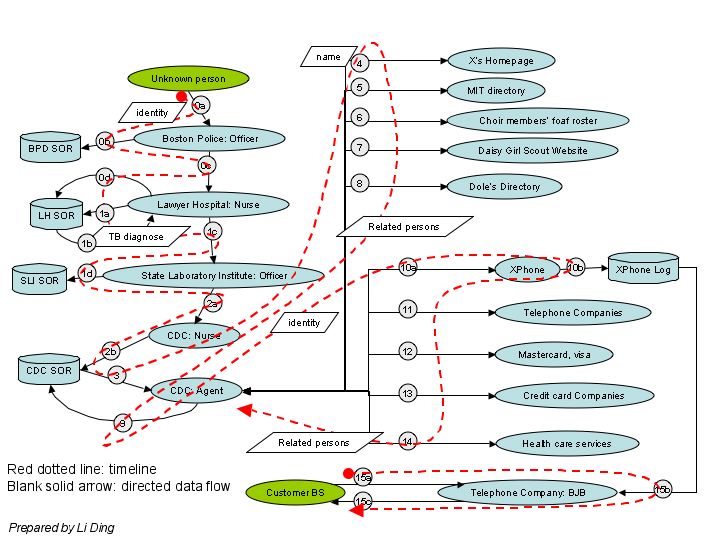
XPhone permits customers to control how and when their personal information is released except when required by law, when served with valid legal process, or to protect the health and safety of customers, employees, or property.
XPhonePolicy1 a rei:Policy;
rei:event { ?C a Customer.
?RE a ReleaseEvent;
source ?S;
destination ?D;
data [ a DataItem; ownedBy ?C ]
};
rei:condition [ rei:constraint { ?RE isrequiredby gov:Law };
rei:result { ?S rei:permitted ?RE } ];
rei:condition [ rei:constraint { ?RE governedBy [ a gov:Subpoena ] };
rei:result { ?S rei:permitted ?RE } ];
rei:condition [ rei:constraint { ?C rei:delegated { ?S rei:permitted ?RE } };
rei:result { ?S rei:permitted ?RE } ].
You can only use data in a System of Records (SOR) if you're using it for the purpose for which it was collected
PrivacyPolicy1 a rei:Policy;
rei:event { ?AE a AccessEvent;
requester ?R;
data ?D.
?D gov:sor ?SOR.
?SOR gov:sorn ?SORN.
}
rei:condition [ rei:constraint { ?R a gov:GovEmployee };
rei:result { ?R rei:permitted ?AE };
rei:future-use { ?SOR purpose ?PURPOSE.
?R responsibility ?RESP.
?PURPOSE a ?RESP } ].
|
|
|
